Changpeng Zhao (CZ) shared a Google warning that “government-backed attackers” tried to steal his password. He posted the alert on X and asked if it linked to the Lazarus Group.
“I get this warning from Google once in a while… North Korea Lazarus?”
he wrote.
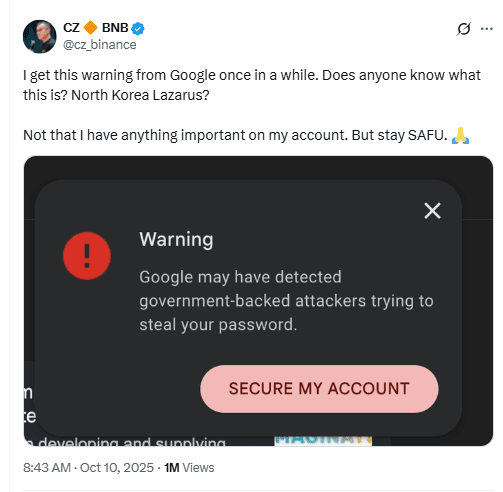
The Google warning indicates targeted attempts against a high-profile account. It points to credential theft as the first step in a broader intrusion. The notice aligns with recent probes against executives in the crypto sector.
Author and adviser Anndy Lian told Cointelegraph a government official he knows saw a similar Google warning.
“They tried to contact Google for more information, but nothing was given due to security reasons,”
he said. His account adds context to repeated alerts tied to government backed attackers.
Lazarus Group track record and the Bybit hack
The Lazarus Group remains linked to multiple crypto incidents. Investigators cite the Bybit hack on Feb. 21 as the year’s largest at $1.4 billion. The case illustrates the scale attributed to North Korean operators.
Open reports outline how Lazarus Group works. They use phishing, fake documents, and malware to steal credentials. They often start with email, then pivot to cloud tools and wallets.
Laundering patterns also recur after large thefts. Mixers, bridges, and rapid chain hops appear in tracing records. Those flows followed the Bybit hack, according to public analyses.
North Korean impersonators, SEAL findings, and CZ’s Sept. 18 alert
On Sept. 18, CZ warned that North Korean agents pose as job candidates. He said they target development, security, and finance roles. The goal is to gain access through standard hiring paths.
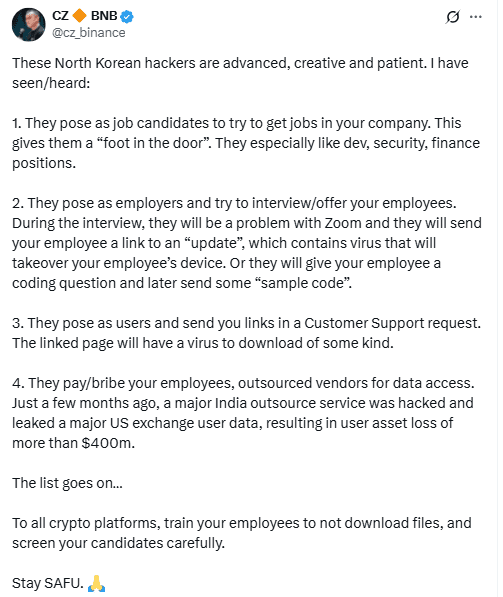
The ethical hacker group Security Alliance (SEAL) published at least 60 profiles. These profiles document North Korean IT worker impersonators using false identities. The list shows coordinated attempts to enter crypto firms.
CZ’s warning and the SEAL repository describe the same vector. They highlight social engineering alongside technical exploits. The overlap supports the view that hiring pipelines are now a frontline.
Coinbase data breach, US intelligence, and remote IT workers
In May, Coinbase disclosed a data breach affecting less than 1% of transacting monthly users. Cointelegraph reported on May 15 that reimbursement costs could reach $400 million. The figures show meaningful exposure even with limited reach.
US intelligence reports describe a network of agents posing as remote IT workers. These agents route earnings and proceeds back to Pyongyang. The activity matches the patterns flagged by SEAL and CZ.
This context situates the Google warning to CZ within a wider campaign. It ties individual account probes to organized efforts. The touchpoints include hiring, help-desk pushes, and identity fraud.
2024 totals, 47 incidents, and the 102 percent increase
Across 2024, Chainalysis estimates $1.34 billion in crypto stolen by North Korean actors. The firm counts 47 incidents, a 102 percent increase from $660 million in 2023. The totals include exchange breaches, bridge attacks, and enterprise wallet compromises.
The data also tracks asset mix and laundering routes. Bitcoin remains significant, but stablecoins feature more in recent flows. These shifts affect tracing timelines and recovery odds.
The Chainalysis figures align with current alerts from platforms. They show sustained pressure on executive accounts and developer systems. Therefore, the Google warning, the SEAL profiles, and the 2024 totals describe the same trend.
